Did you have internet issues last Friday?
Looks like OpenDNS customers didn’t notice a thing.
Pro-tip: OpenDNS users generally see the Internet as they should. We do a good job of handing “last known good” IPs when we can’t resolve.
— ☁ David Ulevitch ☁ (@davidu) October 21, 2016
A modest way of saying, “Today’s wide outage is a perfect reminder of why you should consider working with @opendns.” Just sayin’. https://t.co/tgUZgvzjRm
— Chris Sacca (@sacca) October 21, 2016
We’re glad your internet didn’t break! Read about our innovations here: https://t.co/veZI0kTJZQ https://t.co/sLIyGwCSDS
— OpenDNS (@opendns) October 21, 2016
#Twitter is #NOT #DOWN
CHANGE Your #DNS to #OpenDns
208.67.222.222
208.67.222.220 IT Works 🙂— Micheli F. (@franki_kuka) October 21, 2016
Google Public DNS is not resolving https://t.co/ezjU9Cw7h5. Switch to #OpenDNS if you have problems. https://t.co/iXQ666WsqP
— Pietro De Nicolao (@pietrodn) October 21, 2016
What DDoS attack? #ShakeItOff ? https://t.co/M6Ity7in5g
— OpenDNS (@opendns) October 21, 2016
What is OpenDNS and how did they help these customers?
OpenDNS is a Recursive DNS service that is security centric. OpenDNS will block malicious traffic before it hits your firewall or network.
Let me start with a quick 101 on DNS….
Almost all of today’s network/internet communication are tied to DNS (Domain Name Service). If I want to call my wife and don’t know her phone number, I can ask Siri to call her and she will look up my wife’s phone number and then dial it for me.
DNS is the phonebook for the internet. It connects domain names (google.com) to IP addresses.
There are two main DNS server types, Recursive and Authoritative.
Recursive DNS-is like a telephone operator; they will check multiple phone books to provide you the most accurate local phone number.
Authoritative DNS -will actually create the phonebooks based on data provided from name registrars.
The issues the Internet experienced last week were due to a DDOS attack against an Authoritative DNS service.
http://www.networkworld.com/article/3134057/security/how-the-dyn-ddos-attack-unfolded.html
DNS in action
Say I wanted to go to google.com….
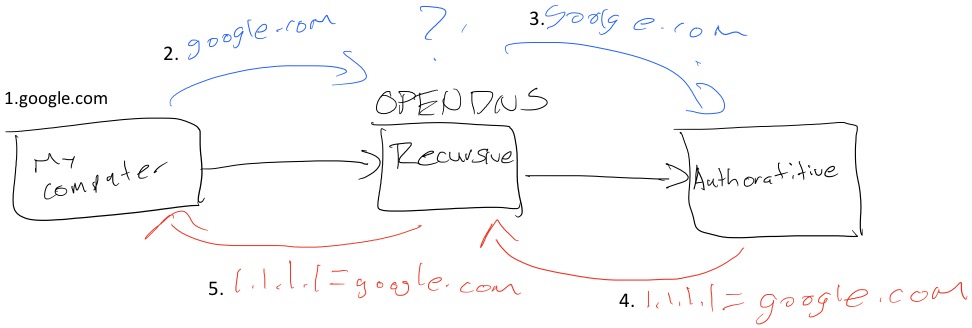
1.My computer would send a request to my Recursive server for the IP address of google.com
2.Recursive server doesn’t have an entry
3.Recursive server forwards request for google.com to Authoritative server
4.Authoritative server responds back to the Recursive server with IP address for google.com
5.Recursive server provides my computer with IP address for google.com (Go to 1.1.1.1 to reach google.com)
What if the Authoritative server is offline? Maybe our Authoritative server was DDOS?
Hopefully you leverage OpenDNS for your recursive DNS service. OpenDNS provides a feature called SmartCache.
“SmartCache uses the intelligence of the OpenDNS network at large, now providing DNS service to millions of people around the world, to locate the last known correct address for a Web site when its authoritative nameserver is offline or otherwise failing. A common occurrence, authoritative DNS nameserver outages often take major Web sites offline for hours or even days at a time, making them inaccessible on the Internet. One recent example of such an outage resulted in popular Web site Amazon.com inaccessible for several hours.”
So in our example, OpenDNS server has the cached entry for google.com and it doesn’t matter that the Authoritative server went down.
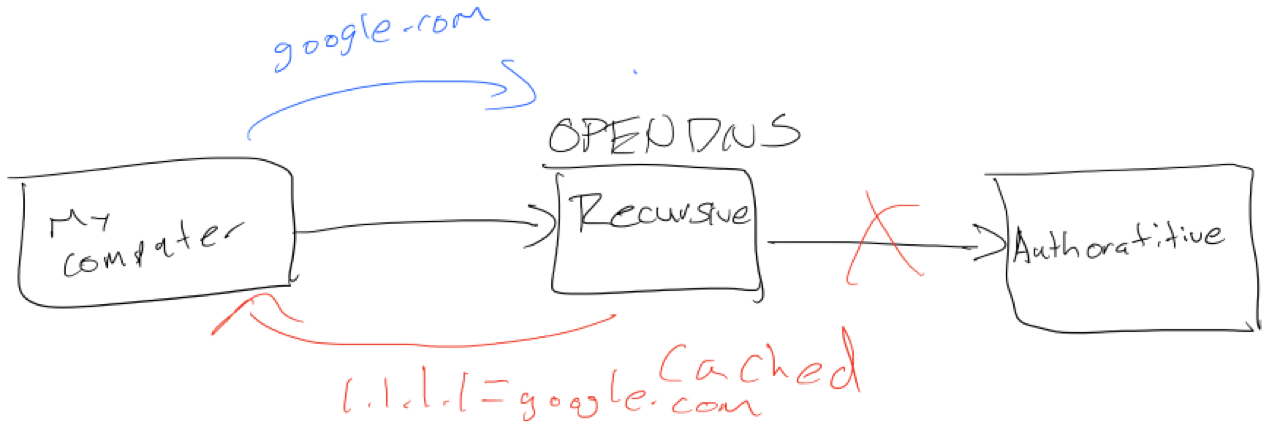 There are many benefits to OpenDNS but one that really stood out last Friday was SmartCache.
There are many benefits to OpenDNS but one that really stood out last Friday was SmartCache.
For me, goodbye 8.8.8.8 and hello OpenDNS.



