When Cisco first acquired OpenDNS I was indifferent. I perceived their service to be free content filtering for home and SMB. After hearing all the buzz, from co-workers, security market, customers etc. I knew there had to be more to OpenDNS.
I learned that it provides an advanced cloud security platform called Umbrella. Umbrella can be used to protect any user or any device, from anywhere, it doesn’t matter if I am sitting in Starbucks or on the corporate network. If you give me a little room here…I like to classify OpenDNS Umbrella as a cloud firewall/gateway that can be used to prevent attacks before it hit your users or network.
The Umbrella Data Sheet states that with Umbrella you can:
- “Reduce malware infections up to 98%”
- “Cut the number of alerts from your IPS, AV, and SIEM by as much as 50%”
- “Decrease remediation time by 20%”
Umbrella in action:
Take for example, I open my email and receive a message from USPSS (which looks like USPS), the title states “check the status of your package.” Knowing that Christmas is coming, I get excited thinking one of my friends sent me a gift. Little do I know the link within my email takes me to a false page, USPSS look alike page, and in the background my computer is reaching out to a known malicious ransomware domain.
If I was using a traditional DNS service, like Google, it wouldn’t block the lookup to the ransomware domain, instead it would provide the ip address for the ransomware domain.

OpenDNS umbrella will block the DNS request for the malicious domain, stopping the attack before it hits my client or network.

OpenDNS has over 65 million users and roughly 80 billion internet request daily. OpenDNS builds security intelligence from internet data, big data analytics, machine learning, and super smart security engineers. With this threat intel, OpenDNS can understand which domains are malicious and block the attack via DNS before it hits your network.
https://umbrella.cisco.com/use-cases/threat-intelligence
https://blog.opendns.com/2015/11/19/opendns-cracks-predictive-security/
https://blog.opendns.com/2015/03/05/opendns-unveils-nlprank-a-new-model-for-advanced-threat-detection/
Umbrella components
1.Cloud Management – Umbrella provides a cloud dashboard…much like Meraki. In this dashboard you can control and manage your security policies and gain visibility into your network traffic. “Umbrella provides visibility into internet activity across all devices, over all ports, even when users are off your corporate network. You can even retain the logs forever.” https://umbrella.cisco.com/products/features
2.Umbrella network protection- To protect your devices on your corporate network simply redirect your external DNS request to OpenDNS. “To switch to Umbrella, you need to explicitly change the DNS settings in your operating system or hardware firewall/router to use IP addresses of the Umbrella name servers and turn off the automatic DNS servers provided by your ISP.”
3.Umbrella Client- To protect your clients off net, you can leverage a lightweight umbrella roaming client. There is even a plugin for AnyConnect VPN, if you are disconnected from VPN your traffic will be protected by OpenDNS.
With Umbrella roaming client, you can also protect IP based traffic. “Alternatively, OpenDNS’s IP layer enforcement provides protection over any port, and from any location through the use of the OpenDNS Roaming Client, an endpoint client that acts as a DNS request forwarder.”https://blog.opendns.com/2015/11/03/opendns-adds-ip-layer-enforcement-umbrella/
More Details AnyConnect Umbrella client
More Detail Umbrella Roaming client
OpenDNS Umbrella is very different from traditional proxy type services. It provides protection across all ports (not just 80/443) without proxying all your traffic to an on-prem device or somewhere in the cloud. “Instead of proxying all requests, Umbrella selectively routes suspicious URLs for deeper inspection. Effectively protect without delay or performance impact.” https://umbrella.cisco.com/products/features/intelligent-proxy
OpenDNS is not a silver bullet but it dramatically can increase security. To me, that is very powerful. The increased security helps to take the load off my firewall, it adds an extra layer of protection to any device anywhere and gain visibility into network traffic.
Stay tuned for my future posts on security and OpenDNS.





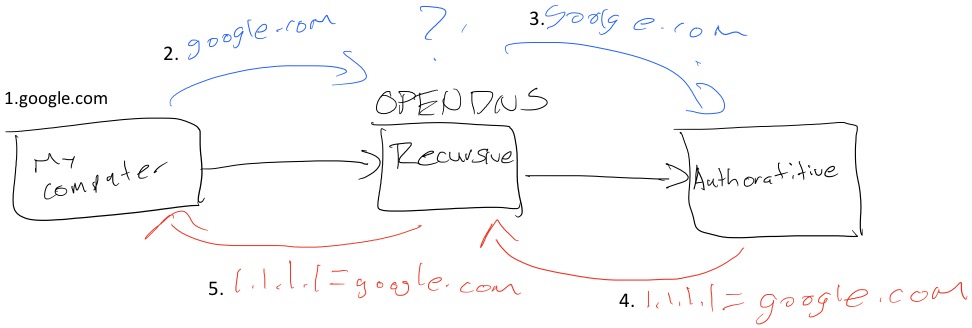
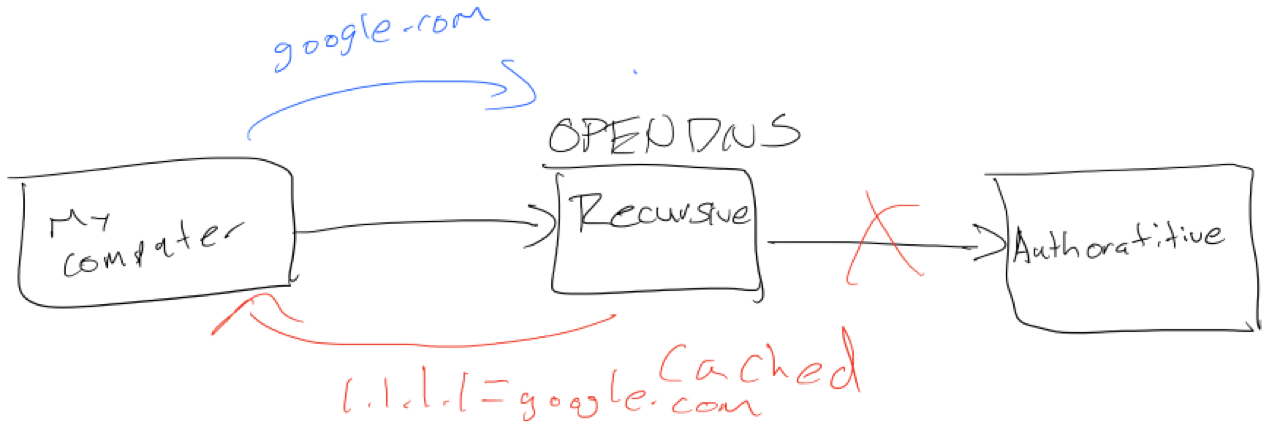 There are many benefits to OpenDNS but one that really stood out last Friday was SmartCache.
There are many benefits to OpenDNS but one that really stood out last Friday was SmartCache.